Cybersecurity Survey Reveals IT/OT Bridges and Disconnects
Claroty, a supplier of industrial cybersecurity software, recently conducted a survey of 1,000 IT security professionals around the globe, including the United States, the United Kingdom, Germany, France, and Australia. One of the major findings highlighted in this study was that the survey respondents, who are typically tasked with protecting enterprise networks, are notably more concerned about a cyberattack on critical infrastructure (65%) compared to an enterprise data breach (35%).
To be frank, I would have been surprised if these number were any different. After all, an attack on critical infrastructure can have immediate or near-term mortal consequences for hundreds or thousands of people, whereas an enterprise data breach—while not to be dismissed—means the interruption of normal business operations until the issue is fixed. So, of course, a cyberattack on critical infrastructure is much worse than an enterprise data breach.
Looking past this data point, the Claroty survey did reveal a number of interesting insights into the state of operations technology (OT) and information technology (IT) cybersecurity. Such as:
- 75% of global (66% of U.S.) respondents have been trained in the differences between IT and OT networks.
- 51% of industry practitioners in the U.S. believe that today’s industrial networks are not properly safeguarded and need more protection, while another 55% believe that U.S. critical infrastructure is vulnerable to a cyberattack.
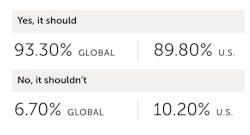
- 93% percent of global respondents think OT-focused cybersecurity should be incorporated into the education and training of IT security personnel.
- 75% of global (65% of U.S.) respondents believe they have the skills to properly manage an OT networks cybersecurity.
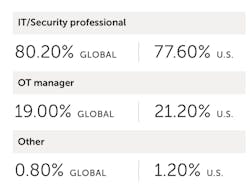
- 80% of global respondents believe it is IT’s responsibility to protect an organization’s industrial network.
Reliance on industrial networks
According to Claroty, it’s imperative that CISOs (chief information security officers) and IT security teams “catch up on the importance of OT security, and how it absolutely does fall into their purview. It is essential to recognize that every company in the world relies on industrial networks. For nearly half of the Fortune 2000—in industries including oil and gas, energy, utilities, manufacturing, pharmaceuticals, and food and beverage—these industrial networks are critical components to their business. The rest rely on these networks for basic needs like transportation, HVAC systems, lights, elevators, and data center infrastructure. These networks are essential and ubiquitous and…collateral damage alone can cost companies billions of dollars.”
These disconnects must be overcome because the “benefits of a secure OT environment are far-reaching and compounding,” Claroty says. “Given the mounting convergence between OT and IT, these benefits include reduced exposure to cyber risks that originate within an OT network but traverse connectivity paths into the IT network. In other words, strong OT security yields stronger OT availability and IT security.”
See the full survey report from Claroty—The Global State of Industrial Cybersecurity.
In related news OT cybersecurity news, Claroty recently announced the integration of its Continuous Threat Detection(CTD) technology with Siemens MobilityData Capture Unit (DCU). The companies claims this integration “provides a hardware and software combination that delivers a highly secure, one-way data flow from industrial networks to corporate IT networks and cloud services. The CTD and DCU combination allows an alternative to not only monitor the traffic for advanced threat detection and visibility but also keep a high Safety Integrity Level (SIL) and maintain a single direction flow of data through industry-leading equipment.”
This combination of technologies operates with Claroty’s CTD passively collecting, aggregating, and analyzing asset and communications data from OT networks and securely transmits them to the corporate network via Siemens' DCU—a hardware implementation of Siemens data diode technology designed “for industrial security and connectivity to eliminate vulnerabilities due to mismanagement and web-based cyber-attacks,” say Siemens. “This allows the DCU to meet all major cybersecurity regulations for critical infrastructure and operate in rugged industrial environmental conditions. Typically located on the edge of the network, the DCU provides boundary protection for the OT network, and a secure bridge when connected to the IT network.”