Industrial Cybersecurity Concerns Heat Up in The Era of COVID-19
As industrial companies connect plant-level software and devices to internet-connected enterprise systems, cybersecurity has become a critical operations issue for manufacturers of all sizes. While the Industrial Internet of Things (IIoT) greatly expands the efficiency of plant floor operations, it also introduces countless new vectors for potential cyberattacks. With more data flowing in and out of plants, the concern is that once localized networks will become more vulnerable.
The threat actors seeking to exploit these new loopholes include disgruntled employees and criminals attempting to steal intellectual property or other sensitive information for purposes of extortion, hacktivists who desire to garner public attention for their causes, and state-backed foreign agents engaged in espionage activities for political purposes.
Unfortunately, the risk of many of these types of attacks has only grown since the onset of COVID-19, according to cybersecurity company CrowdStrike’s recently released 2021 Global Threat Report. This increased hacking activity stems from several sources. For one, as lockdowns took hold in early 2020, many workers migrated to home offices that lacked the cybersecurity protections of commercial workplaces equipped with dedicated information technology (IT) staff. In addition, as remote access boomed, the potential attack surface available to hackers was broadened. Finally, fear and uncertainty surrounding the pandemic has increasingly been exploited to engage in phishing attacks and other forms of social engineering designed to trick users into granting malevolent actors access to proprietary systems and information.
CrowdStrike’s report details recent efforts engaged in by state-sponsored adversaries looking to steal valuable data pertaining to vaccine research and government responses to COVID-19 as well as targeted intrusions, sometimes referred to as “big game hunting.” In these latter efforts, e-criminals identify high-value individual targets for extortion and blackmail via infection with ransomware—software that locks users out of a system until a fee is paid. The report notes that ransomware attacks on manufacturing facilities have proven uniquely effective, as the time-sensitive nature of their production schedules often renders paying the fee less expensive than losing critical throughput.In addition to individual manufacturing facilities, healthcare and the supply chain also stood out in 2020 as particularly vulnerable. In the healthcare space, phishing attacks currently pose the greatest risk, with tactics and techniques taking a plethora of forms, including: exploitation of individuals looking for details on disease tracking, testing, and treatment; impersonation of medical bodies requesting information, including the World Health Organization (WHO) and U.S. Centers for Disease Control and Prevention (CDC); and offering financial assistance or government stimulus packages in exchange for private information.
Meanwhile, cyberattacks on the supply chain have relied on more sophisticated methods. For instance, in December of 2020, public reporting revealed a complex supply chain attack against the update deployment mechanism of the SolarWinds Orion IT management software. Those responsible for this attack were able to distribute malicious code which had the ability to collect information about the host, enumerate files and services on the system, modify registry keys, and terminate system processes. According to CrowdStrike’s report, supply chain attacks represent an especially pernicious tactic because they allow malicious actors to propagate their attack from a single point of intrusion to multiple downstream targets. Following from this, CrowdStrike identifies the securing of cloud environments as a priority for cybersecurity professionals in the years to come.
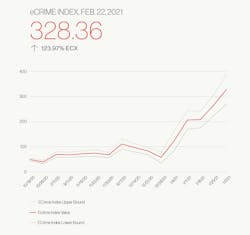
To chart ongoing threats, CrowdStrike has also created an eCrime index based on various observables which are weighted by impact and continuously monitored. The index will allow users to remain aware of the changing mechanisms and tactics used to exploit vulnerable systems and will include additional analysis provided by CrowdStrike’s subject matter experts.