Securing Controls with Defense in Depth
This is the second installment in the new Peer-to-Peer FAQ series of content from Automation World. This series focuses on explaining the most common and trending technologies in the world of industrial automation.
The first article in this series focused on machine vision and smart instrument sensors and how their data can be analyzed using artificial intelligence to improve production operations (access this first installment online at awgo.to/1382). Each installment in this Peer-to-Peer FAQ series will highlight succinct yet detailed explanations of each technology, followed by insights from end users and integrators about their selection, implementation, and use.
This article focuses on cybersecurity, particularly the defense-in-depth approach that has proven to be a successful method of protecting industrial control systems and restoring their operation after a cyber-attack.
Defense-in-depth explained
The use of multiple cybersecurity protections is the key to a defense-in-depth approach to ensure industrial networks remain as secure as possible.
Perimeter-based cybersecurity strategies that employ tools such as firewalls and border routers or that separate plant-floor intranet networks from internet-connected enterprise networks using an industrial demilitarized zone were once recommended as a high-level security tactic to ensure one's information and assets were protected.
However, on their own, these tools are no longer a viable approach in a world where businesses may develop and deploy applications in corporate data centers, private and public clouds, or even leverage software-as-a-service models that require them to maintain a connection to the broader internet. While these technologies drive many aspects of digital transformation, they also create new vectors through which malicious actors can enter a network. Moreover, growing numbers of cybercriminals are using phishing or other means to steal employee credentials. In these cases, networks need to be configured to detect external incursions and identify unusual internal activity.
When a defense-in-depth strategy is properly deployed, even if a bad actor gains access to the network, security protocols exist to prevent them from causing extensive harm. Often, these strategies are applied not only to IT systems, but physical infrastructure and organizational processes as well.
Though expert advice on what constitutes defense-in-depth can vary, following are explanations of the key tools and techniques commonly used to establish a defense-in-depth cybersecurity strategy for an industrial control system.
Network perimeter security
While no longer adequate as a stand-alone method of protection, perimeter-based security mechanisms still play an important role in a defense-in-depth strategy. Tried-and-true perimeter-based methods include firewalls, VPNs (virtual private networks), and VLANs (virtual local area networks).
- Firewalls scan packets entering a network for malicious code that has been identified as an established threat and flags them as security risks when appropriate.
- VPNs mask user data by routing all communications through an encrypted private server, rather than a public internet service provider, allowing users to remotely connect to a network via a secure tunnel. This can be used by someone within a plant who wants to send local data to an enterprise network, or someone outside of a plant who needs to connect to an internal industrial control system safely.
- VLANs are private virtual networks confined to a single plant. They allow a single physical LAN to be partitioned into several smaller units so that industrial automation systems that engage in functions such as real-time control can be separated from internal IT systems used for email or other tasks that require connection to the broader internet.
Although vital as a first line of defense, perimeter strategies can be bypassed by a dedicated hacker. Phishing attempts, physical CDs, USB sticks, or other data carrying hardware devices, as well as blind spots in one's firewall software, can all lead to breaches. Because of this, it's important to employ additional cybersecurity tools.
Endpoint security
The practice of securing entry points to a network is referred to as endpoint security. Because any Internet of Things device connected to a network can serve as an entry point, an Industry 4.0 environment may contain hundreds or even thousands of vulnerabilities.
Endpoint security relies on software packages known as EPPs (endpoint protection platforms), which sometimes include an EDR (endpoint detection and response) component as well. EPPs work by examining files as they enter a network and checking them against a cloud database containing a library of threat information. This allows end users to outsource the cost and burden of storing such large libraries of information on site. In addition, it enables threat libraries to be continually updated based on activity from many different sites.
EDRs augment the EPP by providing a machine-learning algorithm for classifying new threats in realtime. When an EDR is used, abnormal file signatures that may represent a threat can be identified even if no prior record of a similar incursion is contained within the EPP's library. The EDR achieves this by studying the baseline behaviors and tactics common to all known cyber-attacks and scanning for them routinely. This allows new incursions to be detected, even if minor details such as IP addresses, registry keys, and domain numbers vary.
Patch management tools
Patch management is the process of using regular scans and software updates to fix bugs, add new features, or address newly discovered vulnerabilities in an application, system, or network. While this is a well established practice in IT, it is slightly more challenging when applied to operations technology (OT). This is due to a combination of factors, including, but not limited to:
- A lack of automatic inventory monitoring for end systems, making it difficult to determine which assets need updates and when;
- Difficulty in tracking patch releases for all systems and applications, particularly when working in a multi-vendor environment; and
- The time-consuming nature of deploying patches on each individual device, confirming that the updates are working as intended, and documenting the changes.
Intrusion detection and prevention tools
IDS (intrusion detection systems) and IPS (intrusion prevention systems) are like EPP and EDR, with the caveat that rather than merely scanning for malicious files, IDS and IPS track user activity more broadly. This makes them more effective for detecting social engineering attempts that manipulate users into revealing sensitive information.
An IDS works by monitoring user behavior to detect malicious intent, scanning processes when patterns known to be harmful are recognized, and monitoring changes to system settings and configurations. If suspicious activity, a security policy violation, or an inappropriate change to configuration is detected, the IPS takes over. An IPS can drop malicious packets, block offending IP addresses, and kick unwanted users off a network. Whenever one of these actions is performed, the IPS alerts security personnel.
User identity and access management
The goal of identity and access management (IAM) is to grant users access to assets and devices to which they have been pre-approved. This ensures that only trained and vetted users engage with vulnerable or mission-critical applications and systems. Cybersecurity managers can use IAM to limit and control access to sensitive information. A few of the most common are IAM framework components are:
- Privileged Account Management: This refers to the management and auditing of data accessed by user accounts based on a set of privileges that have been granted to them. Simply put, privileged account management allows administrators to create a repository of users which it can assign and remove privileges from based on their role within an organization.
- Multi-Factor Authentication: When information beyond a username and password is required to log in, multi-factor authentication is being used. As an example, after inputting their username and password, a user may be required to enter a code sent via SMS to their smartphone or provide biometric data, such as a fingerprint scan.
- Risk-Based Authentication: When risk-based authentication is used, a system can dynamically adjust the authentication requirements based on the user's situation at the moment the authentication is being attempted. For instance, if a user attempts to access a remote system from a geographic location or IP address that has not previously been associated with them, a risk-based authentication mechanism could require them to confirm their identity by requesting additional information.
- Context-Aware Network Access Control: Like risk-based authentication, context aware network access control is a policy-based method whereby users are granted or denied access to a network based on the context in which they are seeking access. Typical context aspects include user identity, location, device security status, and IP address. Rather than requiring additional authentication steps when a user makes an unusual log in attempt, context aware network access control blocks them entirely.
End user and integrator attack experience
As predicted years ago when news of cyberattacks on large manufacturers began to surface, cyber intrusions have become more widespread across industry, regardless of size of operation or industry vertical.
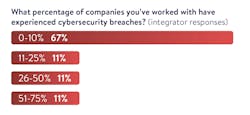
Survey data of Automation World readers in both the end user and system integrator sectors indicate a significant number of system breaches. More than a third of end users (36%) report having experienced a cybersecurity breach at their company. Looking at this question more granularly among system integrator respondents shows that 89% of integrators report up to 50% of their customers having experienced a cyber breach.
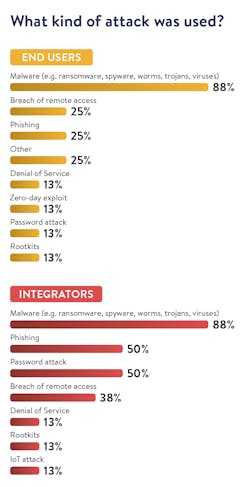
Both end users and integrators note that the predominant form of attack on industrial companies tends to be malware, such as ransomware, spyware, worms, trojans, and other viruses. Beyond these top factors, the response between end users and integrators diverges a bit.
Breach of remote access and phishing were reported as the next most often experienced cyber-attack (each being noted by 25% of end user respondents). Integrators, also noted breach of remote access and phishing, but at a higher rate than end users—38% and 50%, respectively. Only 13% of end users noted experience with password attacks, but 50% of integrators cited experience with this at customer sites.
Best practices to mitigate ongoing issues
When asked about their biggest concerns when it comes to cybersecurity, end users and integrators both cited lasting problems after recovery from an incursion. Specific concerns in this area include:
- Loss of information;
- System access denials;
- Inability to access files; and
- Ongoing interruptions to production.
Ongoing issues have been particularly difficult with ransomware attacks. Rubrik, a cloud data management company, notes the following best practices to apply to any cyber breach recovery scenario:
- Recover safely: Only begin recovery operations after the ransomware has been neutralized. This may mean that data needs to be recovered in isolation or to new systems. Restoring systems or data before the ransomware has been neutralized may result in the system/data being attacked again. If the ransomware cannot be isolated and neutralized in a timely manner, the alternative is to recover where systems cannot be reinfected.
- Decrypt data: Recovery may not be necessary if there is a decryptor for the ransomware strain that was identified. When possible, decrypt existing data to prevent data loss. Decryption should be done in a safe environment. If the ransomware cannot be neutralized, decryption in isolation may be required.
- Isolated recovery: Because ransomware attacks can be so pervasive that recovering back to original locations will only result in secondary attacks, recovering to an isolated environment where the ransomware did not have access is the best prevention against a secondary attack. This requires advance identification and testing of an isolated environment for use during the recovery phase.
- Prioritized recovery: Recovery should be based on prioritization of applications and lines of business. Ensure that foundational services required for basic functionality, such as DNS, DHCP, and authentication are running or restored first. Without these, the recovered systems may not function properly.
- Automation: Automated recovery via tools such as application programming interfaces (APIs) and software development kits (SDKs) will speed up recovery times. Examples of where automation can be particularly helpful include recovery of network-attached storage systems (file level data storage server connected to a computer network to provide access to a group of clients) with tens or hundreds of shares, recovering complete virtual environments with hundreds or thousands of virtual machines, database servers with many databases, and file sets across multiple servers.
Application of defense-in-depth
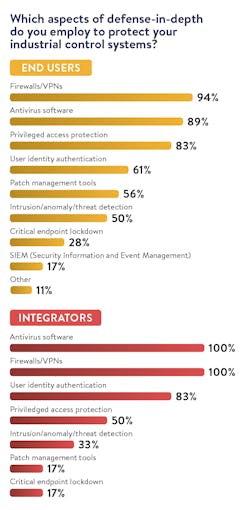
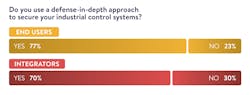
For years now, industrial cybersecurity experts have stressed the importance of the defense-in-depth strategy. Fortunately, this message has not been ignored by industry. Our research shows that 77% of end users and 70% of integrators employ the defense-in-depth approach to cybersecurity, with 44% of end users and 50% of integrators having used the approach for five years or more.
Anti-virus software, firewalls/VPNs, user identity authentication, and privileged access protection are the top four technologies deployed by both integrators and end users in their defense-in-depth approach. Beyond these top four technologies, however, further defense-in-depth technology applications differ between end users and integrators. Though both end users and integrators cite intrusion/anomaly detection and patch management tools as the next two most widely used technologies, 56% of end users use patch management tools and 50% use intrusion/anomaly detection. However, only 33% of integrators use intrusion/anomaly detection and 17% use patch management tools as part of their defense-in-depth approach.
Other defense-in-depth approaches noted by end users include deep network traffic visibility and the use of a data diode between critical infrastructure and the business LAN (local area network). Data diodes are communication devices that only allow one-way data transfer between source and destination networks.
About the Author
David Greenfield, editor in chief
Editor in Chief
David Miller
Former Senior Technical Writer

Leaders relevant to this article: