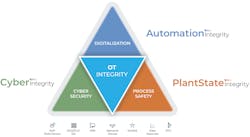
At the 2021 ARC Industry Forum, representatives of PAS highlighted how its software products addressing process safety, digitalization, and cybersecurity complement Hexagon’s industrial software and sensor technologies. Hexagon acquired PAS in late 2020.
Process safety, one of PAS’s earliest emphases, is covered by PlantStateIntegrity, which can now be integrated with Hexagon’s j5 Operations Logbook, an application that allows users to record and manage operational, process, and safety metrics, such as control loop deviations, process disturbances, and alarm frequency. By using PlantStateIntegrity to feed information into the j5 Operations Logbook, complex manual shift handovers can be replaced by the creation of automatically generated digital reports, said Jaclyn Arnold, vice president of owner-operator business at Hexagon. This capability is particularly helpful amid social distancing requirements imposed by COVID-19, which render physical shift handovers not just inefficient, but potentially dangerous.
“One of the biggest [sensor integration] problems is that sensor configuration data resides in multiple sources. The data can reside in a Hexagon SmartPlant Foundation database, it could also reside in an instrument or asset management solution, or in templates provided by a vendor or owner-operator,” Cappi said. “Each of those systems are different technologies provided by different vendors, and they tend to have different users. Those users believe the data they are looking at is the truth, but it doesn’t necessarily reconcile with the other sources. Mismatches in data can lead to unplanned downtime, unit upsets, startup concerns, and a lot of wasted effort going around trying to manually reconcile these data sources.”
Cybersecurity is handled by PAS’s CyberIntegrity platform, which uses the visibility attained by AutomationIntegrity’s discovery capabilities to run vulnerability audits across an organization’s portfolio of field assets. Once potential vectors for attack have been identified, CyberIntegrity is able to inform users of how the weaknesses might be exploited and what can be done to remedy them.
Such cybersecurity concerns are of growing importance as organizations have accelerated adoption of remote access technologies in response to COVID-19. A prime example of the potential threats posed by remote access were spotlighted this week after a hacker gained access to a water treatment facility in Oldsmar, Florida. The hacker attempted to increase the levels of sodium hydroxide, otherwise known as lye, in the city’s water supply, only to be stopped by a vigilant employee who noticed the incursion.
Referring to the incident, PAS Founder Eddie Habibi noted that companies expanding their remote access capabilities should prioritize the development of a complete asset inventory to ensure the efficacy of their cybersecurity risk assessments.
“The cyber threat to critical infrastructure has been increasing steadily as hackers, whether nation-state actors, criminal enterprises, or lone individuals better understand how to exploit OT (operations technology) in addition to IT systems. While much of the coverage of the cyber risk to critical infrastructure to date has focused on the age of many industrial control systems and the fact that they were not designed and deployed with security in mind, in this case, the attack vector appears to have been the increased level of remote access enabled by the Florida county,” Habibi said. “In the rush to support remote operations during the global pandemic, there are very likely many organizations who have increased remote access to industrial engineering workstations and operator consoles … It is a poignant reminder that the best foundation for effective OT cybersecurity is a detailed and broad asset inventory that includes relationships and dependencies among OT systems and a baseline of configuration settings. With this in place, risk assessment is far more informed, enabling organizations to more effectively assign and limit remote access at both the system and account levels.”
About the Author
David Miller
Former Senior Technical Writer

Leaders relevant to this article: