Cloud computing has come a long way in the trust department in just a few short years. Whereas it seemed not so long ago that most people thought manufacturing was no place for cloud services, that viewpoint has changed quickly.
Those who trust public clouds now outnumber those who distrust public clouds by more than 2-to-1, according to the second annual cloud security report from Intel Security. There has been a noticeable shift in that trust level even compared with the first survey one year earlier. “In one year, the IT professionals surveyed have moved away from the feeling that the cloud is untrustworthy, to a better understanding of the benefits that it can bring,” said Raj Samani, EMEA chief technology officer for Intel Security.
Granted, the trust seems to run a bit deeper for some industries outside manufacturing, but manufacturing has become a cloud proponent as well. As in other industries, cloud computing has become ubiquitous for manufacturing, according to Samani. “This demonstrates a fundamental shift in the thinking and belief that cloud computing is only for non-sensitive assets or processes,” he said. “Indeed, the general consensus is that public cloud is more trustworthy than ever before.”
Released this week at the RSA Conference in San Francisco, the survey of more than 2,000 IT professionals across a range of industries shows the current state of cloud adoption, the primary concerns with private and public cloud services, security implications, and the evolving impact of what is known as shadow IT—IT systems specified and deployed without involvement by the IT department.
More than 80 percent of the organizations surveyed said they are now following a Cloud First strategy, meaning that priority is given to applications that can be purchased as a service or deployed in the cloud vs. requiring hardware and physical servers and systems to be deployed in the data center.
“The Cloud First strategy is now well and truly ensconced into the architecture of many organizations across the world,” Samani said. “The desire to move quickly toward cloud computing appears to be on the agenda for most organizations.”
Growing use of cloud computing would seem to be in direct correlation to improved trust and perception of public cloud services. Most organizations view public cloud services as or more secure than private clouds. That improved trust and perception, as well as increased understanding of the risks by senior management, is encouraging more organizations to store sensitive data in the public cloud. “Public cloud benefits are being realized, with the cost of outsourcing compared to hosting internally acting as the key motivator,” Samani said.
According to survey results, 59 percent of respondents indicate that the public cloud is more likely to deliver lower total cost of ownership, 54 percent say it will provide better visibility of their organizations’ data, and 51 percent feel it will be more likely to keep their data safe.
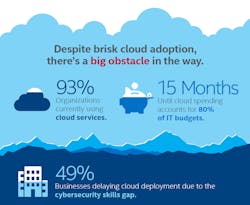
A hybrid of public and private offerings have become more predominant, though. With 93 percent of the organizations surveyed using cloud services in some form, the response has shifted considerably from private-only or public-only to a hybrid architecture. In 2015, 51 percent of respondents were relying on private clouds. While that has dropped to 24 percent in the latest survey results, hybrid architectures have risen from 15 percent to 57 percent. A hybrid model of public and private is even more common in the manufacturing sector, accounting for 65 percent of cloud use.
Cloud deployments could be happening even quicker if companies didn’t face a shortage of security skills in the workforce, according to the IT professionals surveyed. Almost half said that a lack of cybersecurity skills has slowed adoption or usage of cloud services. Another 36 percent say they are experiencing a scarcity of workers skilled in cybersecurity, but are continuing with their cloud activities anyway.
This cybersecurity skill shortage adds to concern for the risks associated with cloud deployment. This shortage could contribute to the prevalence of shadow IT. Because cloud services have become easier to procure, Intel Security explains, almost 40 percent are commissioned without IT being involved. Close to two-thirds (65 percent) of the IT professionals surveyed think this is interfering with their ability to keep the cloud safe and secure.
Regardless of whether cloud computing operates in a public, private or hybrid architecture, attackers will look for the easiest targets, Intel Security noted. “Integrated or unified security solutions that provide visibility across all of the organization’s services could be the best defense,” the report recommends.
Other recommendations from Intel Security:
- User credentials, especially for administrators, will be the most likely form of attack. Organizations need to ensure they are using authentication best practices, such as distinct passwords, multi-factor authentication and even biometrics where available.
- Security technologies such as data loss prevention, encryption and cloud access security brokers (CASBs) remain underutilized. Integrating these tools with an existing security system increases visibility, enables discovery of shadow services, and provides options for automatic protection of sensitive data at rest and in motion throughout any type of environment.
- Organizations need to evolve toward a risk management and mitigation approach to information security. They should consider adopting a Cloud First strategy to encourage adoption of cloud services to reduce costs and increase flexibility, and put security operations in a proactive position instead of a reactive one.
There is considerably more detail in the full report available from Intel Security. For more information, download the report.