We can hear about security breaches in the news like the well-publicized attack on Target’s data. We know about hacker attempts to control systems like Stuxnet, which was only the beginning of a long string of hits. And we all know somebody whose email has been compromised for no apparent reason other than it’s fun to see what you can get into.
And yet so many of us continue to believe that it won’t happen to us.
I don’t know about you, but I have a certain level of trust that our critical power and water infrastructures will not hold that same attitude. And yet, JSUK (just so you know)…
In a recent survey of companies responsible for the world’s power, water and other critical functions, about two-thirds reported at least one security breach that led to the loss of confidential information or disruption of operations in the past 12 months. Granted, I’m going to maintain a certain level of skepticism given that the survey was sponsored by Unisys, which provides IT services, software and technology, so no doubt has something they might want to sell you to combat these issues. However, the survey was conducted by the Ponemon Institute, an independent research and education organization.
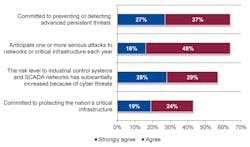
And really, I think the information in itself is pretty telling about the ongoing lack of concern despite the acceptance that the industry overall faces considerable cybersecurity issues. Surveying 599 security executives at utility, oil and gas, energy and manufacturing companies, 64 percent of respondents anticipated one or more serious attacks in the coming year. Despite this risk, only 28 percent ranked security as one of the top five strategic priorities for their organization.
“The findings of the survey are startling, given that these industries form the backbone of the global economy and cannot afford a disruption,” said Larry Ponemon, chairman and founder of the Ponemon Institute. “While the desire for security protection is apparent among these companies, not nearly enough is actually being done to secure our critical infrastructure against attacks.”
Only one in six respondents describe their organization’s IT security program or activities as mature. Respondents who reported suffering a data breach within the past year most often attributed these breaches to an internal accident or mistake, and negligent insiders were the most cited threat to company security.
In fact, the argument I’ve heard most often from readers about why this cybersecurity topic is little more than a lot of hype from companies who want to sell you cybersecurity products is that their companies or the industries they work in are not important enough to warrant a hacker focus. They seem to disregard the threat from within—whether purposeful or accidental. Only 6 percent of respondents said they provide cybersecurity training for all employees.
“Whether malicious or accidental, threats from the inside are just as real and devastating as those coming from the outside,” said Dave Frymier, chief information security officer at Unisys. “We hope the survey results serve as a wakeup call to critical infrastructure providers to take a much more proactive, holistic approach to securing their IT systems against attacks. Action should be taken before an incident occurs, not just after a breach.”
The survey also highlighted the concerns many of these executives feel regarding the security of industrial control systems (ICS) and SCADA systems. When asked about the likelihood of an attack on their organizations’ ICS or SCADA systems, 78 percent of the senior security officials responded that a successful attack is at least somewhat likely within the next 24 months. Just 21 percent of respondents thought that the risk level to ICS and SCADA has substantially decreased because of regulations and industry-based security standards, which means that tighter controls and better adoption of standards are needed.
Most respondents said that they have not fully deployed their IT security programs. Only 17 percent say most of their IT security programs are fully deployed.
For more information, read the full report.
About the Author
Aaron Hand
Editor-in-Chief, ProFood World

Leaders relevant to this article: