Proactive Patch Management
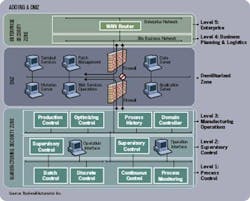
Plants are taking two approaches to proactive security. For one, they’re creating a wall, or demilitarized zone (DMZ) between the company’s business system and the plant system (see chart at right). The business end of the information technology (IT) world is much more vulnerable than the plant side. For example, the plant control system doesn’t have e-mail, which is one common way that viruses and other malicious programs can enter a system. Secondly, control vendors are working to identify vulnerabilities in software before those vulnerabilities are discovered by bad guys.
A secondary DMZ blocks viruses that can enter the business system through e-mail, and then migrate across the enterprise. “Major accounts are deploying a secondary DMZ between the business system and the factory,” says Mike Bush, program manager at controls vendor Rockwell Automation Inc., in Milwaukee. “You have a wall between the business and the outside world, but you also have a wall between the business and the plant. The second DMZ won’t allow a connection to the Internet.”
To further cut the business system from the plant system, some plants are putting the upgrade server inside the secondary DMZ. “We also recommend that plants put their upgrade server in a demilitarized zone between the business systems and the control system,” says Kevin Stagg, engineering fellow for cyber security at automation vendor Honeywell Process Solutions, in Phoenix.
“The frequency of patches is definitely increasing, and so is the risk of losing production,” says Rashesh Mody, chief technology officer at software supplier Wonderware, an Invensys Systems Inc. company based in Lake Forest, Calif. “People want to do the patches without interrupting production.”
One version of proactive security is the effort to detect and patch system vulnerabilities before they are detected by the outside world. “Patching is a little like closing the door after the horse got out,” explains Rockwell’s Bush. “We have network and security services and we do vulnerability tests so we can lock the barn before the horse gets out.”
See the main story that goes with this sidebar:Fixing Software On The Fly