OPC Considerations for Network Security
Cyber security covers the confidentiality, integrity and availability of computers, applications and digital-based assets. In most organizations, this is the responsibility of the corporate Information Technology group. Unfortunately, whenever IT meets real-time control systems, trouble erupts. So when IT implements different Windows domains and firewalls, the first casualty is typically Distributed Component Object Model (DCOM) communication and, consequently, OPC traffic that relies on DCOM.
Microsoft Windows is the most prevalent desktop operating system in the world today, in homes, businesses and industrial facilities. Thus, Windows has become a popular target of malicious network attacks. This is echoed in the fact that hackers constantly develop new worms and viruses that attempt to penetrate every network. These malicious applications are so contagious that the introduction of an infected laptop to an otherwise uncontaminated network can bring an enterprise down in just minutes.
It is for this reason that IT departments are concerned with cyber security. Their objective is to protect the users as well as all the connected devices. Unfortunately, IT departments rarely understand the operational needs of the production side of the business, so communication and compatibility problems, particularly with DCOM, quickly surface.
Microsoft developed DCOM to provide an easy-to-use communication infrastructure for remote Windows applications and computers to work together. DCOM enables developers to reuse Microsoft’s methods and procedures in their own applications. This accelerates application development and increases reliability. It is for this reason that the OPC Foundation selected DCOM as the basic building block for OPC communication.
DCOM originates from the IT side of the world. It is easy for programmers to use, but this ease comes at a price. DCOM requires many ports for finding other hosts, resolving names, requesting services, authentication, sending data and more. If these ports are not available, DCOM will automatically search for others. Of course, any port and service used by DCOM is a target to cyber attacks (viruses and worms), so when DCOM security is compromised, all applications are affected, including OPC applications. The recent Blaster and Sasser viruses attacked the same components that OPC relies upon. Anyone using OPC may be vulnerable to both of these viruses and more in the future.
Cyber security is necessary for process control networks if they intend to integrate with business networks. Again, due to the pervasive nature of Windows and DCOM, when the IT department locks down communication, many applications, including OPC applications, are immediately and frequently terminally affected. The good news is that if plant and business systems are configured and maintained correctly, network security and OPC can coexist.
Addressing cyber security between plant production and business systems is a complex task that most IT and automation groups are hesitant to undertake. IT may not be familiar with complex industrial systems, and any errors can adversely affect production. From the perspective of industrial automation, challenged with IT security they would rather just run autonomously and let a communication "gap" remain between these systems. Industrial cyber security at a minimum requires the focus areas listed below:
• Filtering and access control
• Anti-virus
• Data backup strategies
• Active monitoring and detection
• Written best-practices and policies
• Restoration procedures
• Incident management procedure
• Continual training and awareness
• 3rd-party verification
The short list above is an introduction; there are many more elements to consider. In general, the two important areas are technology and people, and it does not matter which is managed first. The most important thing to remember is that existing corporate IT policies must empathize with the requirements of real-time control systems, and many rules will have to change accordingly.
Network and cyber security should be a priority, making firewalls a necessity, which creates many new challenges for DCOM. Because DCOM requires so many ports to operate, it is very unfriendly to firewalls. Therefore, DCOM is frequently shut out of communication across different networks or left wide open for worm infection.
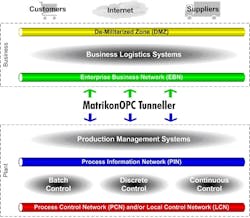
Fortunately, innovative solutions are already available. For instance, OPC can make use of tunneling technology to work across different systems and firewalls. Similar in concept to a VPN (Virtual Private Network) and PPTP (Point-to-Point Tunneling Protocol), OPC tunneling encloses the data payload inside another protocol. From outside the tunnel, it looks like a stream of data. However, inside that stream is the all-important production data. Tunneling technology can also make use of port restriction, user authentication and data-stream encryption to overcome most of the IT security issues. See the graphic for an illustration of how the MatrikonOPC Tunneller, from MatrikonOPC in Edmonton, Alberta, Canada, provides a tunneling solution.
Network and cyber security are very important to industrial systems because they can affect the production of the control system. A complex task requires the aid of experts with field experience. They can recommend solutions for each of the security focus areas, such as OPC tunneling for firewalls. It is important to begin addressing security risks as soon as possible, before they affect production.
For more information on MatrikonOPC, visit www.matrikonopc.com.