Addressing the industrial network vulnerabilities brought to light by the StuxNet virus, a Norwegian network and data security company has extended its proven forensic malware tools into a supervisory control and data acquisition (SCADA) protection product.
Norman ASA (www.norman.com), based outside Oslo, Norway is a pioneer in data security solutions and forensic malware tools and one of the companies who reverse engineered the Stuxnet virus to see how it worked. The company is better known in Europe but competes with Norton and McAfee in the U.S. to supply large multinationals, Internet service providers and others with anti-virus tools and network vulnerability diagnostics. Its industrial customers include Arla Foods, BASF, Boeing, and SonicWall. Its U.S. subsidiary, Norman Data Defense Systems, Inc., is located in Fairfax, Va.
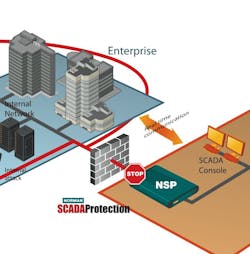
Norman SCADA Protection is the company’s new industrial network protection solution. The hardware/software combination has been designed specifically to protect against Trojans, worms and viruses that might infect industrial SCADA systems.
“Customers say they don’t have bulletproof security. They’re sort of forced to be exposed,” says Oivind Barbo, Norman product director. “SCADA vendors tell users they’re not allowed to have any antivirus software added, because the SCADA system has to update several times a day and could be slowed down. Antivirus software on a PC also can be unpredictable and resource heavy.”
About seven years ago, one of Norman’s industrial customers with several large plants running SCADA software asked if Norman could create an anti-virus front end to scan for viruses. A network appliance device “could live between administration and the IP network, inline between then SCADA network and the rest of the site, and allow them to isolate all malicious code transferred from the outside,” explains Barbo.
Norman invented that appliance, which is Phase 1 of what the Norman SCADA Protection system does—it prevents malicious code from hitting the SCADA network. “We also realized there is another major threat: The people maintaining the networks or getting any kind of physical access to machines. They could innocently or maliciously infect the system. So we also had to protect the physical access, and scan the portable storage devices. This is Phase 2,” says Barbo.
Stuxnet malware has a built-in mechanism for exploiting a security hole in Microsoft Windows. All you have to do is plug in a USB device, without having to log into the target system, and the virus spreads itself. “With Stuxnet, we realized anyone could be carrying the attack vector in their pocket,” says John Callahan, Norman marketing director.
The Norman Protection System makes it impossible for a service engineer or anyone else to plug in any kind of portable storage device without first having it scanned and approved by the network security appliance. A very intelligent piece of software automatically recognizes file systems introduced to the SCADA system and prevents them from mounting and running files.
“Our Malware Analyzer software, which is what we’re known for in the U.S., is a forensics laboratory in a box that lets intelligence agencies and large companies analyze the cyber attacks made upon them,” says Callahan. “Norman Malware Analyzer v2 figures out what malware is trying to do—how it works, where it came from and how to block it in the future. Our Norman SCADA Protection appliances shares some advanced security technology with our Malware Analyzer and builds on that.”
A full functioning system has been successfully running in the field, with all main logic and functionality on the appliance, says Barbo. Callahan said full availability of the product is scheduled for second quarter of this year.
Officials at a water plant in U.S. Midwest recently got alarmed when a maintenance technician traveling in Russia innocently ran remote diagnostics on the plant back in the U.S. Was the intrusion a dry run for a cyber attack from Russia? While the incident proved to be harmless, it raised awareness in the SCADA community of just how open industrial control systems truly are, and how an infection could easily occur as soon as the next maintenance visit.
“That’s exactly the kind of thing we want to prevent,” says Barbo.
Renee Robbins Bassett, [email protected], is Managing Editor of Automation World.
About the Author
Renee Bassett
Managing Editor

Leaders relevant to this article: