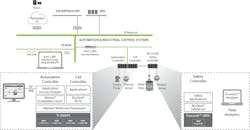
Automation and industrial control system vendors have an opportunity to leverage the Industrial Internet of Things (IIoT) for remote diagnostics and data analytics, which could lead to new revenue opportunities. But with reward comes risk. Opening the lines of communication between a control system and a far-flung field device could also introduce a security threat.
Indeed, IIoT security can’t be an afterthought, which is why electronic design automation provider Mentor Graphics is teaming up with Icon Labs, a supplier of embedded networking and security technology.
This week at the ARC Industry Forum in Orlando, the companies announced the integration of Icon Labs’ Floodgate security products with Mentor Graphics’ Nucleus real-time operating system (RTOS) and Mentor Embedded Linux. Together, the technologies deliver security management and data protection within the operating systems so that devices are secure from the inside out.
Building security directly into devices provides protection that reduces the need for additional security appliances. “Most [companies] in this space focus on securing the perimeter, but that doesn’t protect the endpoint,” says Alan Grau, president of Icon Labs. “It also doesn’t position the device for the future because it provides no visibility.”
The Floodgate framework enables security policy management, event and command audit log reporting, integration with McAfee ePolicy orchestrator (ePO) security management software, an integrated firewall, and firmware and data anti-tamper capabilities-- all of which are natively supported within the Mentor Graphics operating systems.
The built-in security complements the other announcement this week from Mentor Graphics. The new Mentor Embedded multi-platform development tool provides industrial automation developers with integrated and tested capabilities for system partitioning, power management, safety and certification, and more, allowing equipment manufacturers to focus on developing value-add into industrial devices.
Grau says the industrial control system (ICS) vendors recognize the need for security-by-design systems rather than bolt-on offerings, and, as a result, Icon Labs is currently in early stage projects with several ICS vendors.
Today, industrial automation systems include complex connected devices expected to perform important functions, Grau says, and “including security in these devices is a critical design task.” As the number of attacks—and the sophistication of attacks—increase, the need for a comprehensive end-to-end approach to security will be a requirement to ensure devices are protected from future cyber threats, he says.
Leaders relevant to this article: