Manufacturing’s Confusing Approach to Cybersecurity
Cisco has been publishing cybersecurity reports for nearly a decade and its 2017 Midyear Cybersecurity Report has been released amid a flurry of global malware activity across industry. This midyear report notes that the dramatic increase in cyberattack frequency, complexity and size over the past year suggests that the economics of hacking have turned a corner due to the quick and easy access to a range of useful and low-cost resources.
With this reality in mind, Cisco points out that the intent of these reports is to keep security teams and the businesses they support alert to the increasing sophistication of threats and the techniques that adversaries use to compromise users, steal information and create disruption.
Despite the difference in cybersecurity issues across industries, Cisco’s report notes that there are numerous common concerns and, thus, lessons to be learned among industries.
An example of this—and one which Automation World readers will find familiar—is the report’s call to better integrate information technology (IT) and operational technology (OT). “The recent WannaCry ransomware attack caused shutdowns at the Renault-Nissan auto plants in Europe and is an example of how connected systems can be affected by an attack,” the report states. “If connectivity is not done securely and in a coordinated fashion, then even untargeted ransomware can affect OT systems. As connected systems come to the OT world, IT and OT can no longer be walled off from each other. They can benefit by sharing data for analysis to help improve safety and product quality. They can also work together to manage cybersecurity threats. But to do so, they must develop their defense-in-depth capabilities, since disconnected and siloed systems won’t provide a comprehensive view of IT and OT.”
As concerning as cybersecurity breaches are, news about their increasing occurrence appears to be leading manufacturers to improve security. According to the report, 95 percent of the manufacturing security professionals surveyed said cybersecurity breaches have driven improvements at their companies to at least a modest extent. The report also notes that 28 percent of the manufacturers surveyed for the report cited a loss of revenue due to cybersecurity attacks in the past year.
Two key findings in this most recent report of particular interest to manufacturing organizations involve the Internet of Things (IoT) and the supply chain.
Cisco’s report states that one of the biggest vulnerabilities of the IoT is a lack of visibility. The report says that “defenders are simply not aware of what IoT devices are connected to their network. They need to move quickly to address this…because threat actors are already exploiting security weaknesses in IoT devices; [these] devices [then] serve as strongholds for adversaries, and allow them to move laterally across networks quietly and with relative ease.”
Supply chain attacks offer adversaries a way to spread malware to many organizations through a single compromised site, according to the report. In one attack a software vendor’s download webpage was compromised, allowing the infection to spread to any organization that downloaded the software from this vendor.
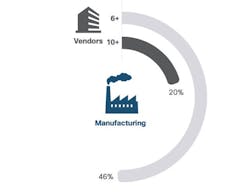
“To get to the point where manufacturing systems are updated and integrated, manufacturers must resolve the security solution complexity problem,” according to the Cisco report. “Forty-six percent of the manufacturing security professionals said they use six or more security vendors; 20 percent said they use more than 10 vendors.” And when asked specifically about products they use from these vendors, 63 percent of security professionals said they use six or more products, while 30 percent said they use more than 10 products. Essentially, they are using one or more products per vendor they are associated with.
This high number of cybersecurity products and vendors in the typical manufacturing facility creates “a confusing picture for security experts,” states the report. “This complexity speaks to the need for both IT and OT teams to narrow their focus on security threats—for example, using only those products than can address the most immediate concerns. Manufacturers could look toward implementing a defense-in-depth policy that includes simple protections for physical assets, such as blocking access to ports in unmanaged switches or using managed switches in their plant network infrastructure.”
Despite the clear increase in cybersecurity breaches that have targeted manufacturers, Cisco says the good news is that there are simple steps manufacturers can take to improve security. The report points out that improving cybersecurity should be seen by manufacturers as being a gradual process rather than a task to be completed all at once. Though something as simple as a written security policy can provide a framework for improvements, the Cisco study shows that 40 percent of the manufacturing security professionals said they do not have a formal security strategy, nor do they follow standardized information security policy practices such as ISO 27001 or NIST 800-53. “
There’s clear room for direct and immediate improvement by simply addressing such best practices.