Should Your Industrial Network Be a Software-Defined Network?
As nearly every other aspect of industrial technology goes digital, so too are industrial networks. And not just the communications that travel across these networks—which have long been digitized—but the networks themselves.
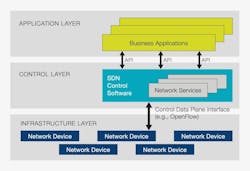
SDN differs from traditional networks that use routers and switches to control network traffic. Instead, SDN creates a virtual network to control traditional network hardware via software.
“Essentially, it transforms network operations to make it more like cloud management instead of physically maneuvering hardware switches, gateways, firewalls and other network appliances, said Chiradeep BasuMallick in an article posted by SpiceWorks.
With SDN’s ability to control the routing of data packets through a centralized server, businesses can “segment different virtual networks within a single physical network or connect devices on different physical networks to create a single virtual network,” according to VMWare. This is a key aspect of using SDN to secure industrial networks.
Why SDN?
At the 2023 Industry of Things World event in San Diego, Jeffrey Smith, chief technology officer at Dynics, discussed using SDN to address industrial cybersecurity. Dynics is a supplier of cybersecurity tools and industrial automation hardware and software.
Another benefit of SDNs, according to Smith, is that it’s impossible to create problematic loops when connecting Ethernet cables to device ports.
Jessica Forguites, technical platform lead at Rockwell Automation, noted that SDN provides additional flexibility to networks when it comes to adding or removing devices or moving devices to different areas of a network. SDN provides “automated network responses to common operations conditions, such as devices being taken out of service for maintenance—which necessitate new communication paths to be established—or establishing connectivity for devices that are moving to different locations of the network,” she said. “SDN helps reduce the workload for network operations teams that manage and monitor networks and it improves response to stakeholders that need to use the network.”
Despite the perception that SDN deployments can be difficult at brownfield sites, Smith noted that his teams have deployed numerous SDN networks in brownfield environments and that implementation was “significantly easier in that [brownfield] situation than any other type of segmentation project for existing systems.” He added that “we deployed in a brownfield about two months ago and it only took two hours from starting to move cables to the new system and configuring the controller to having a fully productive system. We went from a flat network with zero security to having a fully micro-segmented network that was production ready in two hours.”
Smith noted that “even with the advantages inherent in SDN, previous attempts to deploy enterprise SDN solutions in the OT space have been challenging to deploy and often failed. But SDN solutions which are designed for the OT space and include functionality designed with OT in mind, are very successful.”
Smith noted that moves toward SDN in the OT space represent a big shift for plant floor networks because SDN is “not traditional cybersecurity.”
Non-traditional cybersecurity
“I don’t believe zero trust is totally achievable today or at any time within the confines of today’s networking technology,” said Smith, adding that “SDN gets you closer to zero trust than anything else.”
Smith’s reasoning here is based on how SDN microsegments a network, thus rendering VLANs unnecessary. In an SDN, allowed communications are called “flows” and are endpoint device centric.
“With SDN, the network is segmented lower than the physical level—much more so than can be done using other methods,” said Smith. He added that SDNs are “deny by default” because they don’t allow communications between devices outside of permitted flows between specific devices. This level of allowance is why Smith contends that SDN delivers the most zero trust possible network communications.
Another benefit of SDN’s permitted communications is that “if you lose the path between two end points, the flows are recalculated and redeployed to allow continued communication,” said Smith.
This means that keeping track of which ports are used on a device doesn’t matter in SDN, according to Smith. Essentially, “if devices are allowed to talk to each other on network, they’re allowed to talk,” he said.
Forguites added that “it is critical to ensure that policies for network access are monitored and maintained” with any network configuration. “Rockwell incorporates CIP Security across many of our products to help equipment designers/maintainers do this with their control system applications using FactoryTalk Policy Manager,” she said.
OT challenges addressed by SDN
SDN on its own addresses many OT networking and cybersecurity issues, but not all. This is because “SDN networks are configured the way OT folks think about network assets,” Smith said.
A few key capabilities of SDN relevant to an OT perspective include:
- Ability to allow or prevent network device updates based on permissions.
- No network expertise is required of OT personnel to create secure systems. “You can put the controller in learn mode and restrict actions that you see on a list of communications taking place on the network,” Smith said.
- Manage remote access to devices on the OT network.
For example, engineers “often have trouble with certificate exchanges between controllers and I/O,” said Smith. “But SDN levels the playing field because it’s endpoint centric.” Regardless of what vendor devices you’re using, SDN allows one device to communicate with another as directed by SDN.
Any time communications are attempted outside of approved flows, the SDN provides nearly real time notification because the network fabric itself is making the notification, not an auxiliary device or software.
This means there are no issues with installing new equipment if that’s allowed in your SDN architecture, he added.
“SDN controls the connections and protocols while maintaining a security posture,” said Smith. “If [new equipment additions are] allowed, you’ll get notified—within milliseconds—of the change with an information-rich visual network topology and an updated list of end point assets.”
As noted by David Smit of system integrator Interstates in a column written for Automation World, “Plant controls engineers might be change-averse, but SDN’s policy-based rules are attractive to people who are constantly having to engage IT to reconfigure devices to different switches or ports. With user-friendly SDN, devices can be moved to other switches or networks by the controls engineers, giving them more freedom.”
Forguites added that she sees software-defined WANs (wide area networks) being used heavily for WAN connectivity in industry. “This carries a lot of benefit due to the dynamic nature of WAN connectivity,” she said. “Also, for applications that require wireless connectivity, these concepts are being leveraged for end device mobility needs and the benefits associated with the use of common policies for connectivity as devices get moved around.”
Despite its configuration and cybersecurity advantages, Smith cautioned that SDN should not be viewed as a “silver bullet” when it comes to network security as it does not provide for access control—an aspect of network cybersecurity that’s becoming more popular across industry.
Access control is not supported by SDN because SDN can’t tell who is logged into someone’s laptop accessing the network. “However, [tools such as] Veracity’s SDN Controller for OT adds functionality that helps facilitate more user-centric control,” Smith noted. “You can stop and prevent what shouldn’t happen before it happens.”