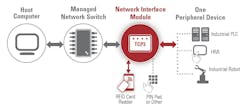
RFID as an Industrial Cybersecurity Method
Cybersecurity has been a major automation topic ever since Ethernet networks began coming down to the plant floor. Most industrial cybersecurity discussions center on a combination of networking and software-oriented approaches to segment and protect critical production operations and systems.
Sometimes overlooked in these cybersecurity discussions is physical access to systems. User authentication is one aspect of secure system access through which authorization data can be used to determine if the employee has the proper skill set and is currently trained and certified to access the manufacturing system hardware and software.
Chris Randle, vice president of industry solutions for Elatec Inc., a supplier of RFID read/write technologies, explains that authorized personnel typically include “plant engineers, maintenance electricians, and IT personnel who can access software running specific processes. The level of access each of these workers has varies according to the individual’s function in the plant. Engineers usually have full access to upload, download and change controller and HMI software. IT personnel usually have only upload or download authorization for backup and disaster recovery purposes. Plant maintenance electricians typically have limited access to change software and only for process troubleshooting. The specific authorization may vary from plant to plant, but identification of who accessed the software, who made changes, and at what time is logged in a database to track changes for review when necessary.”
“Authentication and authorization systems for access control to software in industrial automation applications in factories today require that they be easy to use, flexible, durable, secure, and stand up well to environmental elements,” said Randle. “RFID card systems address these application requirements better than magnetic stripe cards, smart cards (with embedded chips) and PIN pads.”
Because RFID cards are touchless, requiring the user to just wave the card within a few inches of the reader to be read, RFID authentication and access control is considered an easy step for users.
He also noted that, when enabled with network access, RFID readers can communicate using various communication protocols, including gigabit Ethernet, with information technology systems and industrial automation applications like industrial programmable controllers, HMIs, and robots. In addition, RFID card systems are considered more secure than other card-based identification technologies, as data transfer between cards and readers and message traffic between card readers and plant networks can be encrypted.
“RFID readers and cards can also execute a kill command if the card is lost or stolen,” said Randle. “Since the kill command deactivates the card, it prevents unauthorized access to sensitive data, hardware, and software that controls industrial manufacturing processes and hazardous areas in the plant.”
About the Author
David Greenfield, editor in chief
Editor in Chief

Leaders relevant to this article: