OPC UA Builds In Security Functions
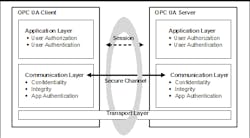
Welcome to the November 2006 edition of OPConnect, the official newsletter of the OPC Foundation. In this issue, I discuss the importance of system security, and how we’ve added security functionality to the OPC UA specification. In the early days of OPC development, the OPC Foundation and its members neglected to address security. We were under the illusion that the operating system security would be sufficient for many of the OPC-based solutions that were being deployed. When we finally realized that the operating system security—or lack thereof—was insufficient for even the control system, it was already too late. We did create an OPC security specification, but that had virtually zero adoption in the marketplace. The reality was that the OPC security specification was too little, and came too late, for vendors to choose to adopt it. With the development of the OPC Unified Architecture specification—and its vision for scalable, cross-platform and enterprise connectivity—we needed to address security in the base set of OPC UA services, in order to succeed. Adding security to the OPC UA services has an impact on performance. OPC UA needs to have a strategy and complete security architecture that provides end-users with the configuration flexibility to turn security parameters on and off, according to application requirements. An additional requirement is to have configurable access control that is scalable in small devices. OPC UA Security Architecture The resulting OPC UA security architecture is a generic solution that allows implementation of the required security features at various places in the architecture. Depending on the different mappings, the security functionalities are addressed at different levels. The OPC UA security architecture is structured in an Application Layer and a Communication Layer, atop the Transport Layer, as shown in the diagram. The routine work of a client or server application—to transmit plant information, settings and commands—is done in a session in the application layer. The application layer also manages the security functions of user authentication and user authorization. The security functions that are managed by the Application Layer are provided by the Session Services that are specified in Part 4 of the OPC UA specification. A session in the Application Layer communicates over a secure channel that is created in the Communication Layer, and relies upon it for secure communication. All of the session data is passed to the Communication Layer for further processing. Although a session communicates over a secure channel, the binding of users, sessions and secure channels is flexible. Impersonation allows the user of the session to change. A session can have a different user than the user that created the secure channel. To survive the loss of the original channel and resume with another, the implementation of the communication channel is responsible for re-establishing the connection without interrupting the logical secure channel. The Communication Layer provides security functionalities to meet confidentiality, integrity and application authentication as security objectives. The provided security functionalities, together with negotiated and secret information, are used to establish a secure channel between a client and a server. This logical channel provides encryption to maintain confidentiality, signatures to maintain integrity, and certificates to provide application authentication for data that comes from the Application Layer and passes, as “secured” data, to the Transport Layer. The security functions that are managed by the Communication Layer are provided by the Secure Channel Services, and are implemented by a protocol stack chosen for the application. Mappings of the services to some of the protocol stack options detail how the functions of the protocol stack are used to meet the OPC UA security objectives. The Communication Layer can represent an OPC UA protocol stack. OPC UA specifies two alternative stack mappings that can be used as the Communication Layer. These mappings are UA Native mapping and Web Services mapping. If the UA Native mapping is used, then functionalities for confidentiality, integrity, application authentication and the secure channel are similar to the TLS/SSL specifications. If the Web Services mapping is used, then WS Security, WS Secure Conversation and XML Encryption are used to implement the functionalities for confidentiality, integrity and application authentication, as well as for implementing a secure channel. The Transport Layer handles the transmission, reception and the transport of data that is provided by the Communication Layer. In this way, the necessary security services are embedded in the OPC UA protocol stack to form a complete security architecture, while still granting users the configuration flexibility needed to serve a variety of applications. For more information, visit the OPC Foundation Web site at www.opcfoundation.org.