Solutions Emerge to Prevent Control System Cyber-Attacks
On February 14, 2012, several new software exploits were released into the cyber-wild that specifically targeted programmable logic controllers (PLCs) from GE, Rockwell Automation, Schneider Electric and Koyo. One exploits also targeted the Ethernet/IP protocol employed by numerous additional vendors, which could allow an attacker to crash or restart affected devices. The U.S. government, taking the problem as a serious threat, issued an advisory the following day.
Weeks later in March, another advisory warned of a threat that continues today: Unknown hackers have been actively accessing the systems managing the natural gas pipeline infrastructure in “what appears to be an information gathering attack,” Joel Langill, chief security officer, SCADAHacker, Appleton, Wisc., said at The Automation Conference in Rosemont, Ill., May 22 and 23, 2012.
The hacktivists, as they are known, are everywhere. And they’re not just infiltrating websites and corporate offices. And that is why the the U.S. Department of Homeland Security's Industrial Control Systems-Cyber Emergency Response Team, or ICS-CERT, issues advisories to makers and users of industrial controls.
What not to do if you’re infiltrated
There are some obvious risks to consider in attacking security holes. Poorly controlled internal user access, system modifications or omissions can compromise security. Consider that companies take every day when they specify, purchase and install controllers: “The majority of PLCs are currently ordered with Web services enabled, but 87% of users leave the Web servers active, unused (and not configured), with factory default passwords,” according to Langill.
Security holes like these leave companies open to the more rare but still-real threat of intentional, targeted attacks. Because every day, somewhere, opportunistic hackers are trying to gain unauthorized access to poorly protected files; perform Denial of Service attacks and sending “spoof” emails that masquerade as legitimate to help them gain access to environments lacking sufficient authentication mechanisms.
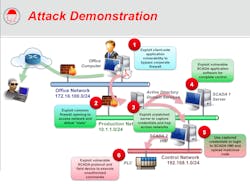
Six attack points – and defenses
Langill explained that industrial control systems, plant information and enterprise networks can all be the source of an attack. In simulated demonstrations of attacks on industrial networks, he illustrated six high-risk exploits where hackers can infiltrate. These are shown in the adjoining “Attack Demonstration” diagram. They are:
Rather, he, ICS-CERT and experts recommend against “lateral network movement," or removing or deleting files. What's needed is to collect forensic evidence, followed by steps that include reviewing and enhancing logging and auditing procedures, doing better network segmentation (firewall and related protections) and improving credential management processes.
The specifics of fending-off threats can be daunting, but Langill stressed one completely non-technical imperative for management to put in place business continuity plans that spell-out how to handle an incident if and when one occurs. He also encourages management to set milestones for “quick wins” as part of a larger, more comprehensive strategy, rather than trying to implement the full strategy at once. A good starting point, he says, should be a critical area such as network segmentation.
Langill has posted a video demonstration of a "supposedly isolated," networked PLC being infiltrated.
In related news, also at the conference, Eric Byres, chief technical officer and vice president of engineering with Tofino Security, Lantzville, B.C, Canada, demonstrated how viruses attack a PLC-based system lacking Deep Packet Inspection via an USB memory stick. This is highlighted in a short video.
For further education, Langill referenced the “Twenty Critical Security Controls for Effective Cyber Defense” (http://www.sans.org/critical-security-controls) from the SANS (SysAdmin, Audit, Network, Security) Institute, a private research and education organization closely aligned with corporations, universities and government agencies including the U.S. State Department, which has used these Top 20 Controls to reduce “measured” security risks 94%, according to SANS.
About the Author
Bob Sperber
Special Projects Editor
Bob Sperber
Special Projects Editor

Leaders relevant to this article: